Articles
Unlocking my apartment with my face
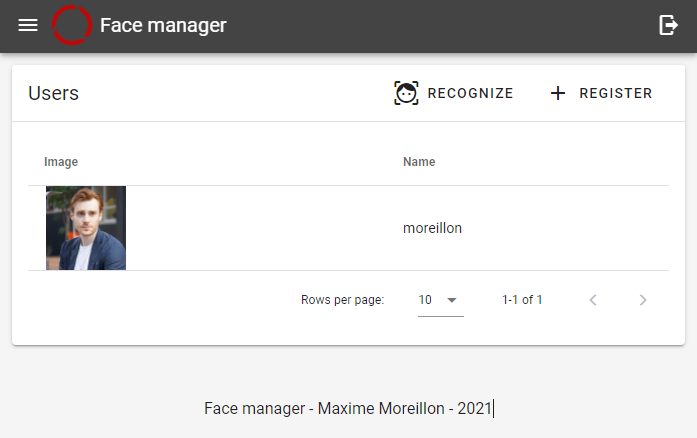
As part of a previous project, I installed an IoT lock on my front door, which allowed me to control it using my smartphone. However, having to take out my smartphone every time I want to unlock the door quickly becomes annoying. To improve on the situation, I installed an RFID reader on the lock, which I used in combination with an RFID ring which now serves as my key. To follow up on this trend of finding new ways to unlock my door, I decided to explore face recognition technologies.
Tensorflow 1.X basics
Here are the basics steps necessary to write TensorFlow code.
Python list slicing
Here are a few useful features of Python when dealing with lists (Arrays):
Python virtual environments
When working on multiple python projects, dependencies might conflict. For example, a project might use version 1.5 of Tensorflow while another uses version 2.1.
Inheritance in Python
Let's imagine that we have a python class as follows (Python 3):
0 - 10 / 5